
Holistically Protecting Your Salesforce Data: A Three-Bucket Strategy
Because in the realm of data security, especially concerning Salesforce, understanding the holistic approach to data protection is not just beneficial – it’s essential.
This article explores how data masking is key to strengthening your Salesforce security. Learn how this simple yet powerful method helps keep your data safe from breaches and meets compliance standards.
Why This Matters
In light of recent cybersecurity incidents in Australia and New Zealand, understanding Salesforce security, including Salesforce data masking, is more crucial than ever. It’s essential for any organization processing private data, especially under GDPR and CCPA regulations.
Salesforce mandates multifactor authentication (MFA), a critical security layer. Consider using a VPN to restrict access to your Salesforce org, ensuring that users log in from secure, corporate devices.
The heart of Salesforce security lies in data management. Collect what you need, regularly remove unnecessary data, and always secure what you retain. This approach aligns with privacy laws and reduces the risk of data breaches.
Security awareness should be ongoing, not a one-time event. Educate your teams about security best practices within and outside the workplace. Utilize resources like Salesforce’s Trailhead for continuous learning.
Regular health checks using Salesforce’s built-in tools can help identify potential security gaps. For a more nuanced understanding, especially in complex environments, consider engaging experts like Doug Merrett for specialized assessments.
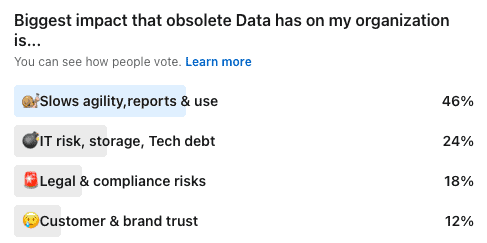
In the dynamic landscape of Salesforce data management, discerning the value and liability of data is crucial.
A staggering 70% of data in many Salesforce systems is obsolete, carrying hidden costs that can impede organizational agility, inflate storage expenses, skew AI models, and disrupt sales pipelines.
In contrast, only about 30% of the data actively contributes to revenue generation and business operations. This disparity highlights the need for a strategic approach to data management in Salesforce.
Data, like any asset, has a diminishing return over time. Initially, data brings significant value, driving informed decision-making and strategic insights.
However, as time progresses, the relevance and utility of data often decrease, turning it into a liability rather than an asset. This shift necessitates a proactive stance in data management, ensuring that only pertinent and valuable data is retained.
Protecting data in Salesforce sandboxes is crucial. DataMasker, a tool developed by Cloud Compliance, offers an effective solution for Salesforce data masking, ensuring that sensitive information is protected even in development environments.
Dev sandboxes often contain real user data, including email addresses and phone numbers. With thousands of users, the risk of exposing sensitive information is significant.
Data masking becomes essential to protect this data while allowing developers to work with realistic datasets.
Why risk exposing user email addresses and other personal information in Dev sandboxes? Implementing data masking is a proactive step towards adhering to security best practices.
While Salesforce’s Shield Platform Encryption adds an extra layer of security, it’s essential to understand its scope. It encrypts data at the Salesforce database level, addressing specific contractual and legal requirements.
Implementing robust security measures in Salesforce involves several steps.
Cloud Compliance’s Privacy Center on AppExchange automates retention policies, helping organizations comply with privacy laws. It’s essential to regularly review and update these policies to align with evolving regulations and business needs.
Salesforce security is an ongoing journey, not a destination. As technologies and threats evolve, so should your security strategies. Engaging with experts, utilizing the right tools like Salesforce data masking, and fostering a culture of security awareness are key to safeguarding your Salesforce environment.
Download the free guide on how to “Secure your Salesforce Org for 0$“
Book a Demo with Cloud Compliance for more insights and detailed strategies on Salesforce security, including Salesforce data masking sandbox techniques.

Saurabh is an Enterprise Architect and seasoned entrepreneur spearheading a Salesforce security and AI startup with inventive contributions recognized by a patent.
DataMasker can mask about 100 million records in 24 hours, handling 3 to 5 million records per hour on Salesforce.
Salesforce rigorously tests these apps. Each app and its updates must pass Checkmarx scans to identify and fix vulnerabilities, ensuring secure coding practices.
Organizations should ensure these apps have only the necessary access and permissions. While Salesforce checks app security, organizations must assess security, especially for apps with off-platform features.
On-platform solutions run in your Salesforce Org, which means that your data never leaves your Salesforce. This means you do not have to worry about other vendor’s 3rd party infrastructure and can reduce potential of data breach risks.
AppExchange security approved apps such as DataMasker from Cloud Compliance comply with Salesforce’s rigorous security standards.

Because in the realm of data security, especially concerning Salesforce, understanding the holistic approach to data protection is not just beneficial – it’s essential.

Disclaimer: To all readers, please note that this not legal advice, nor is this coming from Salesforce. This is strictly my personal opinion and perspective
Marathon runners obsess over their socks and shoes – because to outdo their past performance, they need to take advantage of everything at their disposal.

Reducing Salesforce data footprint directly reduces the cost and risks of potential data leaks and embarrassment, as well as benefits your organization. Here are

We earlier talked about reducing production data. The third step to reducing data in your Salesforce org is to define retention policies. The idea here

We talked earlier about masking sandboxes. The second step is to reduce production data. The idea here is that obsolete information in your Salesforce production

Why should you mask data in Salesforce and what kind of data should you be masking to ensure security, compliance and trust. Let’s take
This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
Strictly Necessary Cookie should be enabled at all times so that we can save your preferences for cookie settings.
If you disable this cookie, we will not be able to save your preferences. This means that every time you visit this website you will need to enable or disable cookies again.
This website uses Google Analytics to collect anonymous information such as the number of visitors to the site, and the most popular pages.
Keeping this cookie enabled helps us to improve our website.
Please enable Strictly Necessary Cookies first so that we can save your preferences!
This website uses the following additional cookies:
Please enable Strictly Necessary Cookies first so that we can save your preferences!
More information about our Cookie Policy