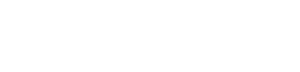Step 1: Open the ‘Configuration’ window
Click on the ‘Configure’ button on the Installed Packages page.
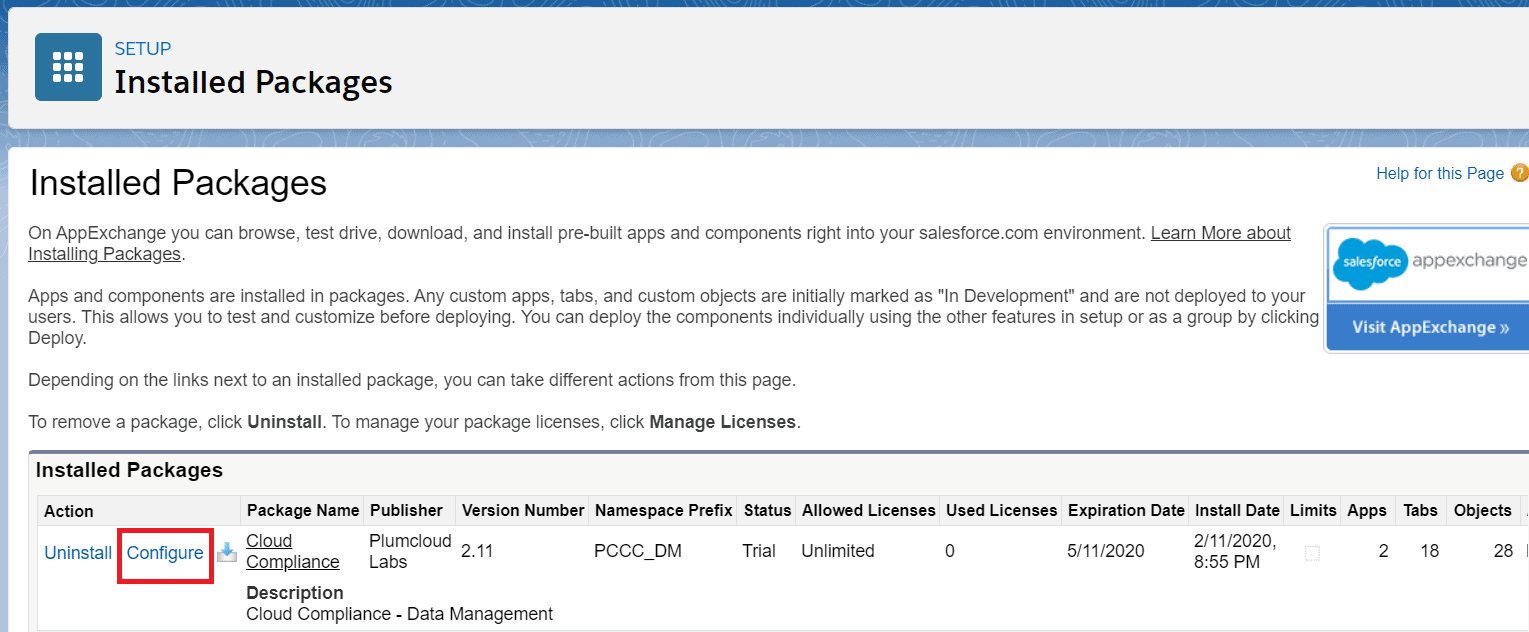
Step 2: Select the De-identification option
After clicking the ‘Configure’ button, a new window will open displaying four options –
- De-identification
- Self Service
- Debugger
- Trigger
The crypto technique is located in the De-identification option, so you’ll need to select De-identification.
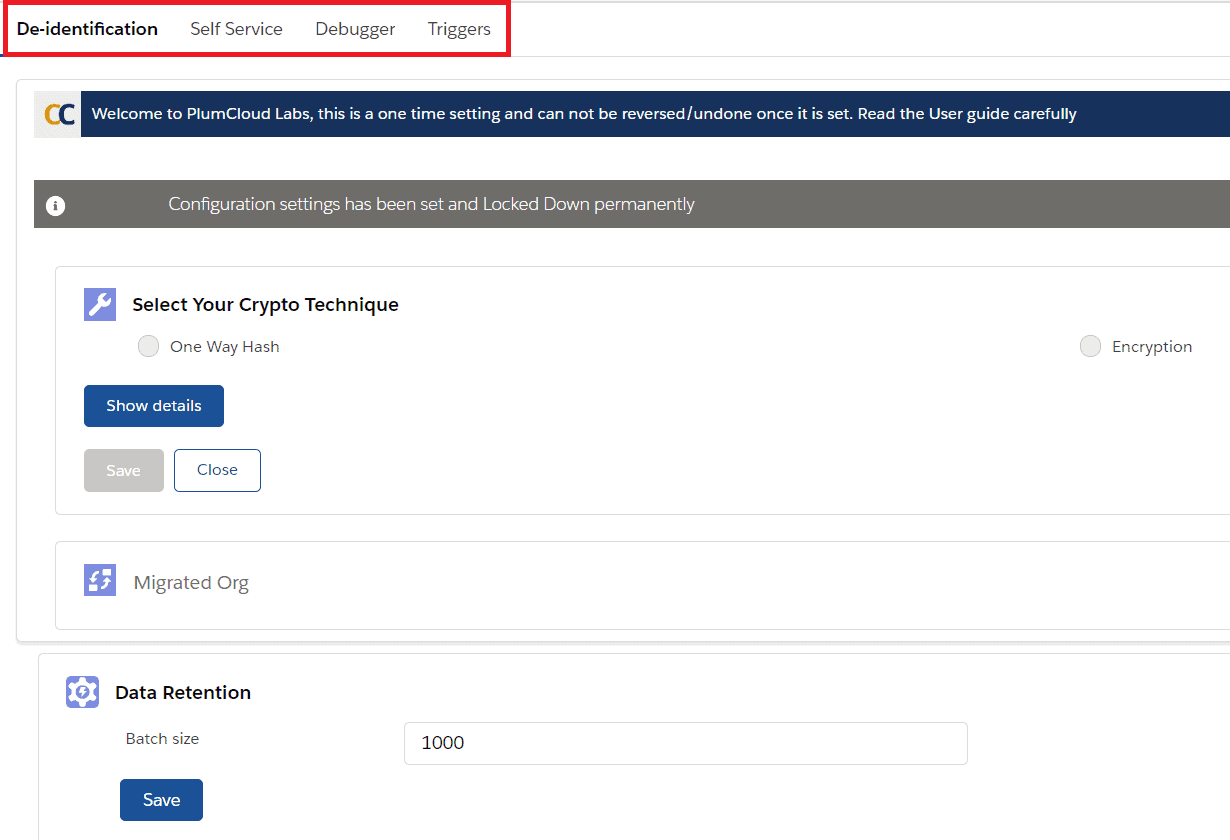
Step 3: Select the Crypto Technique
You’ll need to select the crypto technique to securely store ‘proof of de-identification. Cloud Compliance creates and secures ‘proof of de-identification by storing it in an encrypted format using one-way hash or encryption techniques.
NOTE: Once the crypto technique is selected, it cannot be changed.

Step 4: Pick an Encryption Method
One-way hash method: ‘Proof of de-identification information from the original de-identified record is not accessible in a clear text format. It can only be searched against.
Encrypted method: ‘Proof of de-identification information from the original de-identified record is displayed in a clear text format. It can be searched against and the original values can be viewed with appropriate access.
NOTE: Refer to the table below and determine the crypto approach that suits your company’s data regulation policy.
| Crypto Technique | Description | Reference | Advantages |
| One-way Hash | One way hashed records cannot be unencrypted. | Refer to Salesforce Documentation Creating Hash Digests | Search only returns a confirmation of whether the searched value was part of a de-identified record and the Id(s) of the original record(s) This method is ideal when a ‘proof of de-identification is the only identifier needed. |
| Encryption | Encrypted records can be de-encrypted. The search returns a complete decrypted record. | Refer to Salesforce Documentation Hash-Based Message Authentication Codes (MAC) | This method is less secure compared to the one-way hash. A search returns all fields of the record as unencrypted data. Ideal for customers that need information beyond a ‘proof of de-identification identifier for auditing purposes. |